The July 2025 release of the fourth revision of the NIST Digital Identity Guidelines marks a turning point in the evolution of digital security standards. NIST SP 800-63-41 is not just a technical update, but a strategic response to emerging threats that have shaped the cybersecurity landscape in recent years, with particular focus on sophisticated phishing and social engineering attacks that have compromised even enterprise organizations with advanced security controls.
The timing of this revision is no coincidence: over the past three years, we have seen an escalation of attacks exploiting weaknesses in traditional multi-factor authentication implementations, proving that SMS OTP and non-cryptographic hardware tokens can be bypassed with increasingly sophisticated man-in-the-middle techniques.

The modular structure #
The fourth revision maintains the modular approach introduced in version 3, consisting of four distinct volumes addressing complementary aspects of digital identity management2:
- SP 800-633: The base volume defining the Digital Identity Model, risk management principles, and fundamental terminology
- SP 800-63A4: Identity Proofing and Enrollment, covering identity verification and user registration processes
- SP 800-63B5: Authentication and Authenticator Management, dedicated to authentication mechanisms and authenticator lifecycle management
- SP 800-63C6: Federation and Assertions, defining protocols for federation and assertion management
This article specifically focuses on the base volume and SP 800-63B5, which covers authentication and authenticator management, central elements for any modern enterprise IAM strategy.
The importance of these standards extends beyond U.S. borders. In Europe, NIST SP 800-63 serves as a fundamental technical reference inspiring directives such as NIS2 and DORA, providing a pragmatic framework to implement effective security controls. Multinational organizations often use NIST SP 800-63 as a common baseline to standardize security controls across different jurisdictions, significantly simplifying governance and multi-regional compliance.
The convergence between U.S. and European standards is accelerating, with ENISA explicitly referencing NIST for specific technical aspects, creating a global ecosystem of shared best practices7.
Why it represents the future of Authentication #
SP 800-63B defines the technical requirements for user authentication and authenticator lifecycle management, introducing a risk-based approach balancing security and usability through three Authenticator Assurance Levels (AAL)8:
- AAL1: Single-factor authentication based on “something you know” (passwords, PINs)
- AAL2: Multi-factor authentication requiring at least two distinct authentication factors
- AAL3: Multi-factor authentication with mandatory phishing resistance
The true innovation lies in the risk-adaptive approach allowing organizations to dynamically adjust authentication controls based on session context, user, and resource sensitivity9. This means the same user can experience different authentication requirements depending on a real-time risk score.
The integration of behavioral analytics and threat intelligence in decision-making marks a significant advancement over traditional static controls that applied uniformly regardless of operating context.
AAL Levels and authenticator requirements #
| AAL Level | Authentication Factors | Authenticator Types | Phishing Resistance |
|---|---|---|---|
| AAL1 | Single factor (“something you know”) | Memorized secrets (passwords, PINs) | Not required |
| AAL2 | Two distinct factors - at least one “something you have” | Memorized secrets + one of: • OTP hardware/software • Out-of-band device • Cryptographic software authenticator (e.g. passkeys) |
Optional (recommended) |
| AAL3 | Two factors with one “cryptographic hardware” | • Cryptographic hardware authenticator (e.g. FIDO2 security keys, PIV smart cards) • May include “something you know” for multifactor |
Mandatory |
Evolution from v3 to v4 #
The transition from version 3 to 4 introduces paradigm shifts reflecting evolving threat landscapes and technological progress. A comparative analysis highlights most important transformation areas:
| Key Change | NIST SP 800-63-3 | NIST SP 800-63-4 | Technical Rationale |
|---|---|---|---|
| Risk Management Process | Static risk assessment at enrollment | Continuous evaluation and cross-functional engagement10 | Need for dynamic threat response and team-based approach |
| Identity Proofing Controls | Basic IAL levels with limited flexibility | Restructured controls with expanded fraud requirements11 | Address synthetic identity attacks and injection threats |
| Phishing-Resistant Authentication | Recommended only for AAL3 | Required options for AAL2, mandatory for AAL312 | Rising sophistication in phishing attacks and OMB M-22-09 compliance |
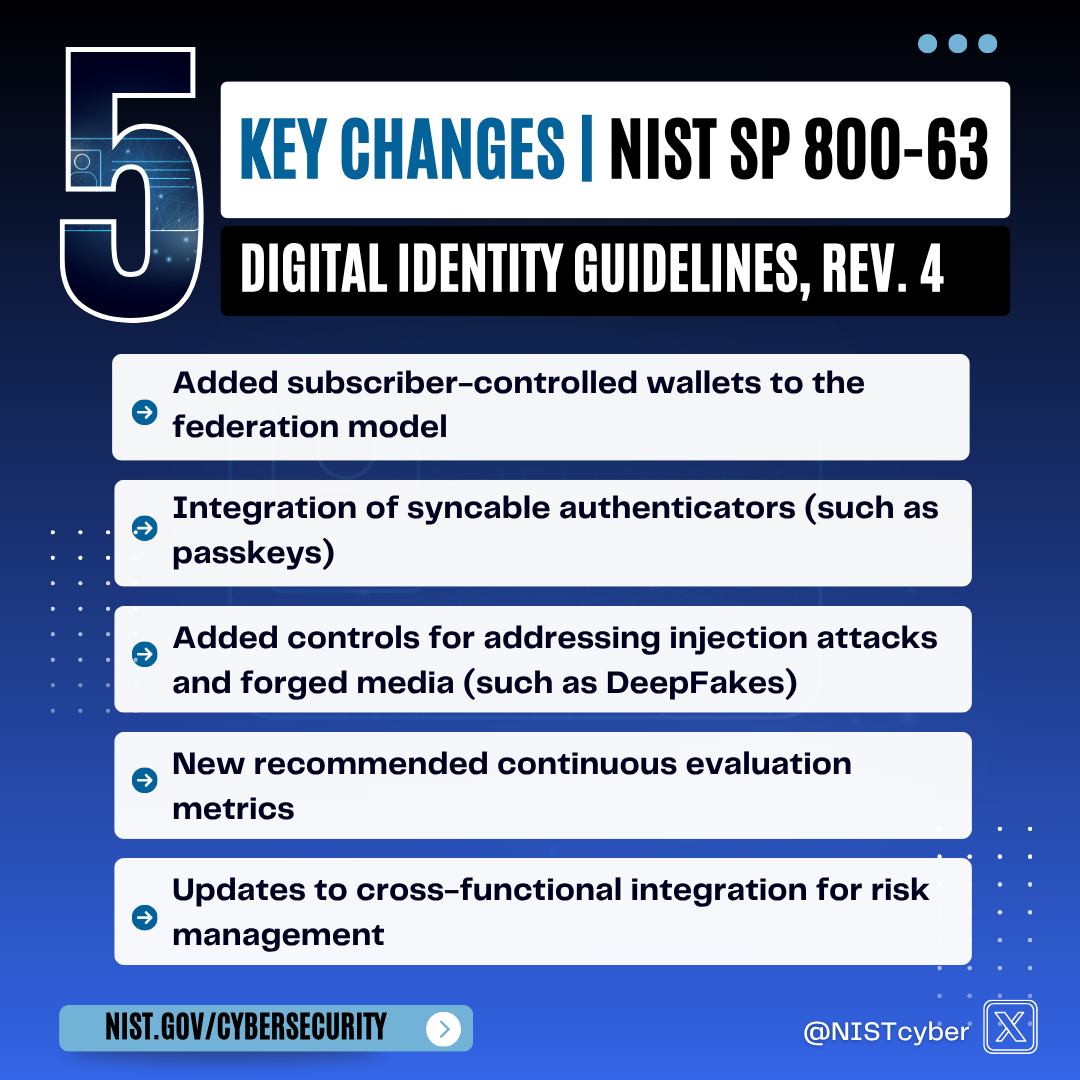
| Syncable Authenticators | Not considered | Explicit support for passkeys and cross-device sync13 | Enable modern passwordless user experiences |
| Password Expiration | Recommended periodic expiration (90 days) | Strongly discourages forced expiration11 | Research shows insecure behaviors with frequent rotations |
| SMS/Voice OTP | Limited for AAL2+ with exceptions | Further deprecated with strict limitations14 | Increasing vulnerabilities to SIM swapping and interception |
| Subscriber-Controlled Wallets | Traditional federated model only | New federation model with user-controlled digital wallets6 | Support for emerging verifiable credentials and decentralized identity |
Key innovations #
Beyond the comparative framework, NIST SP 800-63-4 introduces fundamental innovations that redefine enterprise authentication. Here’s how these changes translate to real-world implementations.
Digital Identity Risk Management (DIRM) #
NIST SP 800-63-4 introduces the revolutionary concept of “continuous evaluation”10 in identity risk management, transforming security posture from reactive to predictive through continuous intelligence.
The framework sets specific requirements for continuous evaluation15:
- Real-time risk scoring based on behavioral analytics
- Threat intelligence integration identifying compromise indicators
- Adaptive authentication controls dynamically adjusting requirements
- Comprehensive audit trails for forensics and compliance
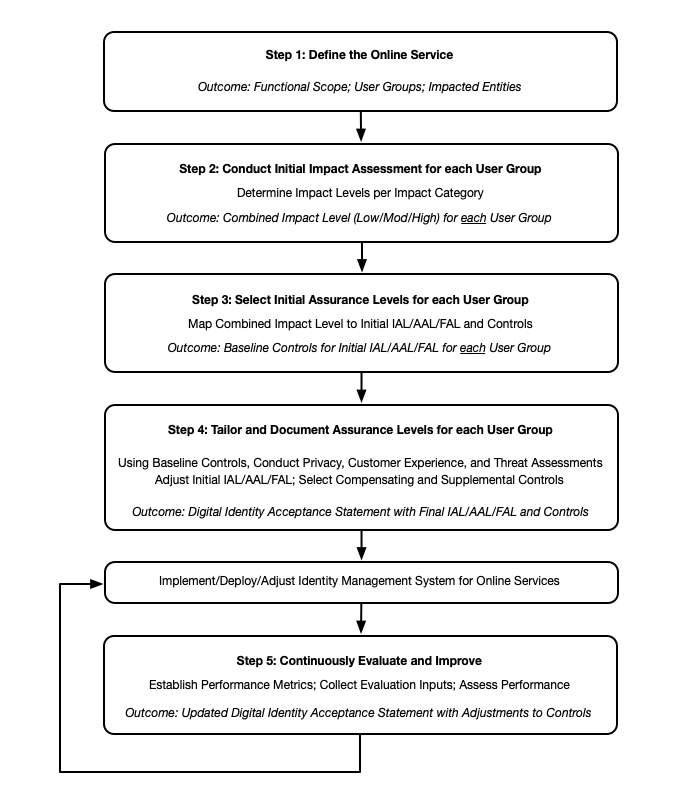
To operationalize this vision, NIST defines a structured five-step DIRM process ensuring continuous, risk-based control of digital identity:
- Define the Online Service Document service scope, user groups, and assets to establish context for risk analysis.
- Assess Service-Level Risks Identify risks arising from the online service itself — data sensitivity, threat landscape, and potential impacts.
- Assess Identity-System Risks Evaluate risks introduced by the identity solution — fraud vectors, privacy concerns, and usability factors.
- Select and Tailor Controls Choose baseline controls (IAL/AAL/FAL) and tailor them via compensating or supplemental measures based on your risk assessments.
- Monitor and Reassess Continuously Execute continuous evaluation, update risk assessments, and adjust controls as threats and service requirements evolve.
Okta’s integrated platform directly supports this NIST framework through two complementary solutions that - in addition to well-know features like SSO and Adaptive MFA - address the DIRM process:
- Okta Identity Security Posture Management provides continuous monitoring via:
- 360-degree identity visibility across cloud, on-premises, and hybrid environments
- Risk scoring algorithms considering over 200 identity risk factors
- Automated remediation workflows for immediate threat response
- Compliance automation maintaining posture alignment with multiple frameworks
- Okta Identity Threat Protection delivers detection and response intelligence via:
- Machine learning models trained on global threat intelligence
- Behavioral baselines for each user-device combination
- Real-time threat blocking for known malicious IPs and patterns
- Investigation workflows supporting security teams
Integration of ISPM and ITP creates a closed-loop security system identifying risks, implementing compensating controls, and verifying mitigation effectiveness in real time — precisely the outcome NIST SP 800-63-4 envisions for modern Digital Identity Risk Management (DIRM).
The end of password expiration #
NIST SP 800-63-4 definitively ends the era of passwords expiring every 90 days11, based on a decade of behavioral research showing such practices adversely affect security.
Studies cited by NIST demonstrate forced password expiration systematically leads to:
- Predictable incremental patterns (password123, password124, etc.)
- Cross-system reuse to reduce cognitive load
- Voluntary weakening of passwords to ease memorization
- Shadow IT behaviors like writing down passwords in insecure locations, or non-approved Password Managers
The modern approach favors complex yet stable passwords, supported by continuous monitoring systems that identify compromise indicators without requiring arbitrary rotation16.
This paradigm shift aligns perfectly with Okta’s strategy, where Okta Identity Security Posture Management continuously provides visibility into credential-related risks through:
- Breach database correlation for compromised password detection
- Weakness analysis based on entropy and pattern recognition
- Usage analytics for identifying dormant accounts or login anomalies
- Automated compliance reporting for audit and governance
Okta and Auth0 further strengthen this approach through Breached Password Detection capabilities, automatically scanning credentials against comprehensive databases of compromised passwords, eliminating the need for arbitrary password rotation while maintaining robust security posture.
Phishing-Resistant Authentication #
One of the most significant revolution is the mandatory introduction of phishing-resistant options for AAL212, a direct response to attacks showing traditional controls’ ineffectiveness against sophisticated phishing campaigns.
Phishing-resistant authenticators rely on cryptographic proof of origin that mathematically binds authentication to the application’s specific domain. This entails:
- Origin binding through TLS channel attestation
- Public-key challenge-response protocols
- Replay protection via cryptographic nonces
- Device attestation to verify authenticator integrity
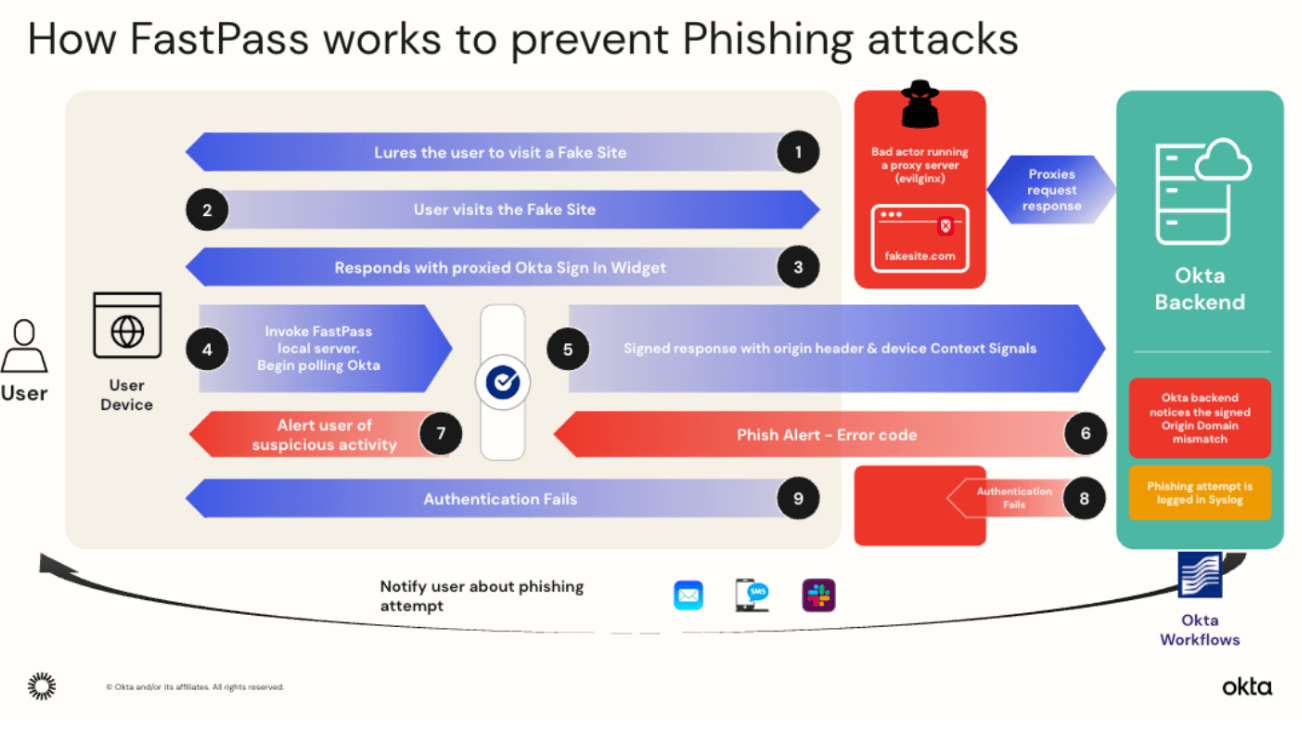
Okta FastPass is the most advanced market implementation of this paradigm in the enterprise. Built on FIDO2/WebAuthn principles but extended across the Okta app ecosystem, FastPass features:
- Device-bound cryptographic keys generated and stored in hardware security modules
- Automatic origin verification preventing man-in-the-middle attacks
- Transparent fallback mechanisms for legacy applications
- Centralized policy management for scalable deployment17
Native integration with the Okta ecosystem means FastPass works immediately with thousands of SaaS applications without app modifications — a competitive advantage over traditional FIDO2 implementations needing per-app integration.
Syncable Authenticators / Passkeys #
NIST SP 800-63-4 explicitly introduces support for “Syncable Authenticators”13, an innovative category solving the portability problem of cryptographic credentials across multiple devices while maintaining high security standards.
Specific requirements for syncable authenticators include18:
- End-to-end encryption during synchronization
- Device attestation for every endpoint accessing keys
- Secure key derivation preventing key extraction
- Audit logging to track synchronization events
Passkeys represent the most mature implementation of this concept, combining FIDO2/WebAuthn security with cloud-based syncing managed by platforms (iCloud Keychain, Google Password Manager, Microsoft Authenticator).
Okta offers the most comprehensive enterprise passkey support on the IAM market, featuring:
- Cross-platform registration flows adapting automatically to device capabilities
- Intelligent fallback chains guiding users to the most secure available authenticator
- Enterprise policy controls governing passkey usage in business contexts
- Analytics and adoption tracking to measure deployment success19
Okta manages user experience complexities automatically, such as handling access from unsynced devices and migrating users gradually from legacy authenticators.
Connected Authenticators #
“Connected Authenticators” represent the natural evolution of traditional hardware tokens, encompassing devices connecting via USB, NFC, or Bluetooth but implementing modern cryptographic protocols20.
NIST SP 800-63-4 recognizes these devices as the gold standard for AAL3, especially in high-risk contexts where physical authenticator separation is critical. Benefits include:
- Hardware-based key storage preventing key extraction even after device compromise
- Tamper resistance certified under FIPS 140-2 Level 2+
- Multi-protocol support for legacy and modern application compatibility
- Enterprise management capabilities for bulk provisioning and lifecycle management
Okta’s connected authenticator integration is native and comprehensive, covering the entire available hardware security key ecosystem, with particular excellence in YubiKey support:
YubiKey Example #
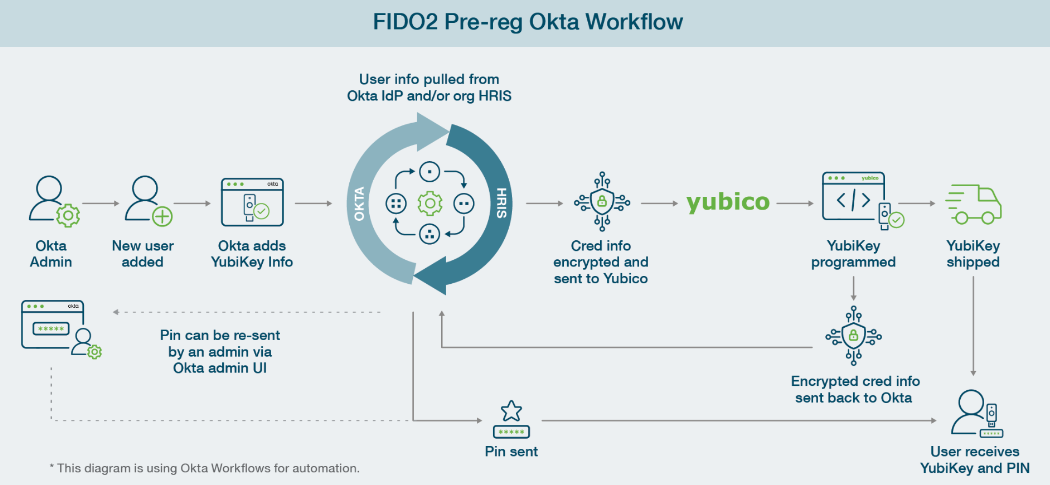
Okta provides the market’s most advanced support for Yubico YubiKey devices, managing the full lifecycle with enterprise-grade features:
- Pre-enrollment & distribution
- Centralized bulk provisioning of hundreds/thousands of YubiKeys
- Secure direct-to-employee shipping with verifiable chain of custody
- Automatic activation on receipt, no IT intervention
- Custom packaging with corporate branding
- Lifecycle management
- Automated inventory tracking and usage monitoring
- Backup policies requiring multiple keys per critical user
- Automated replacement workflows for lost/damaged devices
- Compliance reporting for audit trails
- Technical integration
- Full FIDO2/WebAuthn support across all YubiKey models
- PIV/smart-card compatibility for government use cases
- Legacy OTP modes for older applications
- Mobile NFC authentication
- User experience
- Guided setup wizard and automated troubleshooting
- Certified multi-browser support
- Offline authentication capability
Okta’s approach transforms a traditionally complex and labor-intensive process into an automated, scalable experience, significantly reducing deployment costs and improving user adoption.
Biometrics Delegation: pragmatism in Platform Trust #
Rather than mandating detailed biometric standards, NIST SP 800-63B focuses on accuracy, privacy, and liveness detection requirements, allowing organizations to leverage proven platform-level implementations21:
- Apple Secure Enclave for on-device fingerprint/Face ID processing22
- Windows Hello with TPM-backed anti-spoofing23
- Android StrongBox for isolated biometric template storage24
- Samsung Knox for hardware-backed biometric verification25
This pragmatic approach lets enterprises benefit from the billions invested by platform vendors in biometric security, rather than reinventing complex systems in-house.
Okta Verify leverages this evolution, providing seamless integration with all major platform authenticators, ensuring optimal user experience without compromising security. Features include:
- Automatic platform detection for optimal authenticator selection
- Progressive enhancement using available biometric capabilities
- Fallback mechanisms for devices without biometric support
- Policy controls governing biometric use per security level
SMS OTP Deprecation #
The decision to further restrict the use of SMS and voice OTP14 responds to concrete evidence of compromise. SIM swapping attacks have exploded globally, with the UK experiencing a staggering 1,055% surge in unauthorized SIM swaps in 2024 according to Cifas, rising from just 289 cases in 2023 to almost 3,000 cases26. Meanwhile, SS7-based exploits continue to enable real-time SMS interception27.
NIST SP 800-63-4 specifies SMS OTP can only be used if:
- The organization implements real-time anti-fraud monitoring
- A documented risk assessment process is in place for each deployment
- Compensating controls mitigate known vulnerabilities
These requirements make SMS OTP deployment so complex that it’s practically inadvisable for most enterprise organizations.
Implementation Challenges #
Adopting NIST SP 800-63-4 involves complexities requiring strategic planning and disciplined execution. The three main challenge areas include:
- Legacy Application Modernization - Most enterprise applications lack native support for modern authentication protocols. Migration strategy should consider:
- Implementing identity gateways to wrap legacy authentication flows - solutions like Okta Access Gateway provide seamless integration with legacy applications without requiring code modifications
- Progressive enhancement gradually introducing phishing resistance
- User education campaigns for smooth transitions to new methods
- Risk assessment frameworks for prioritizing application migration
- Organizational Change Management - Transitioning to passwordless and phishing-resistant authentication requires cultural transformation beyond technology adoption:
- Executive sponsorship to drive organization-wide adoption
- Training programs for IT staff on new protocols and troubleshooting
- Scalable user support to manage increased help desk volume during migration
- Defining success metrics to measure adoption and security improvements
- Compliance Orchestration - Multi-jurisdictional organizations must orchestrate compliance requirements across frameworks:
- Mapping NIST SP 800-63-4 controls to regional requirements (NIS2, DORA, etc.)
- Automating evidence collection for audit preparation
- Policy harmonization to avoid conflicting requirements
- Vendor assessment processes ensuring solution compliance
The role of Integrated Platforms #
Fragmented implementation of NIST SP 800-63-4 requirements across multiple vendors introduces operational complexity and security gaps potentially compromising the entire security strategy.
Gartner research shows organizations with more than five identity vendors spend 40% of their security budget on integration and maintenance, leaving insufficient resources for innovation and threat response28.
The strategic response is a unified platform approach managing the entire digital identity lifecycle through:
- Single pane of glass management reducing operational overhead
- Native protocol integration eliminating custom development
- Unified analytics and reporting for complete security posture visibility
- Scalable deployment models supporting organizational growth
The Okta ecosystem delivers this integration via:
- Okta Workforce Identity:
- Auth0
- Okta FastPass
- Native passkey support
- Okta Identity Security Posture Management (ISPM)
- Okta Identity Threat Protection (ITP)
These solutions embody Okta’s **Secure Identity Commitment**m — delivering market-leading products and services, championing customer best practices, and fostering an open identity community that continuously advances security standards.
Business Impact #
Implementing NIST SP 800-63-4 through integrated platforms delivers measurable ROI across multiple vectors:
- Security ROI
- Breach prevention: The 2024 Verizon Data Breach Investigations Report shows that 68% of breaches involve the human element, with credential-based attacks being the most common vector29
- Incident response reduction: Automated threat detection significantly reduces investigation and response times according to industry studies30
- Compliance automation: Organizations report substantial reductions in audit preparation time with automated evidence collection31
- Operational ROI
- Help desk reduction: Gartner research indicates that 20-50% of help desk calls are password-related, with each reset costing organizations $70 on average32
- Provisioning automation: Forrester research shows enterprise identity platforms can save organizations significant operational costs through automation33
- Vendor consolidation: Multiple identity vendors create operational overhead and integration complexity34
- User Experience ROI
- Productivity improvement: Studies show employees spend approximately 11 hours annually managing passwords and authentication35
- Mobile experience optimization: Native platform authenticators reduce authentication friction
- Adoption acceleration: Okta customer studies demonstrate improved user satisfaction with modern authentication methods36
Preparing for the future #
NIST SP 800-63-4 lays the foundation for future security evolutions, with emerging trends shaping the next generation:
- Quantum-Resistant Cryptography or Post-Quantum cryptography (PQC)
While NIST SP 800-63-4 emphasizes cryptographic agility, organizations should note that NIST is actively preparing for post-quantum cryptography transitions through separate initiatives, with implementation expected by 203037.
Okta Ventures has identified post-quantum cryptography as one of five key focus areas for 2025, actively seeking innovative companies with unique approaches to future-proof identity infrastructure against quantum threats. Recent breakthroughs from leading quantum computing research have accelerated timelines, making post-quantum readiness more urgent than previously anticipated38. - Decentralized Identity Models
Verifiable credentials and blockchain-based identity represent the move toward user-controlled identity, with NIST developing specific guidance for these paradigms39. Both Okta and Auth0 actively participate in the Decentralized Identity Foundation, contributing to standards development for self-sovereign identity solutions. - Protocol Security Evolution: IPSIE
The Interoperability Profiling for Secure Identity in the Enterprise (IPSIE) initiative represents the maturation of OAuth 2.0 and OpenID Connect for enterprise use. As organizations implement NIST SP 800-63-4’s authentication requirements, IPSIE provides critical guidance for secure federation protocol implementation, eliminating common vulnerabilities while ensuring cross-vendor interoperability.
AI-Powered Adaptive Authentication #
NIST SP 800-63-4 formally acknowledges the role of artificial intelligence and machine learning in modern identity systems40, particularly in Section 3.8 which addresses the opportunities and risks of AI/ML integration. The guidelines emphasize that AI systems should enhance rather than replace traditional security controls, while ensuring transparency and accountability in automated decision-making processes.
The NIST framework specifically calls for organizations to:
- Implement explainable AI models that can provide clear rationale for authentication decisions
- Establish human oversight mechanisms for high-risk automated decisions
- Continuously validate AI model performance against evolving threat patterns
- Ensure fairness and avoid bias in AI-driven risk assessments
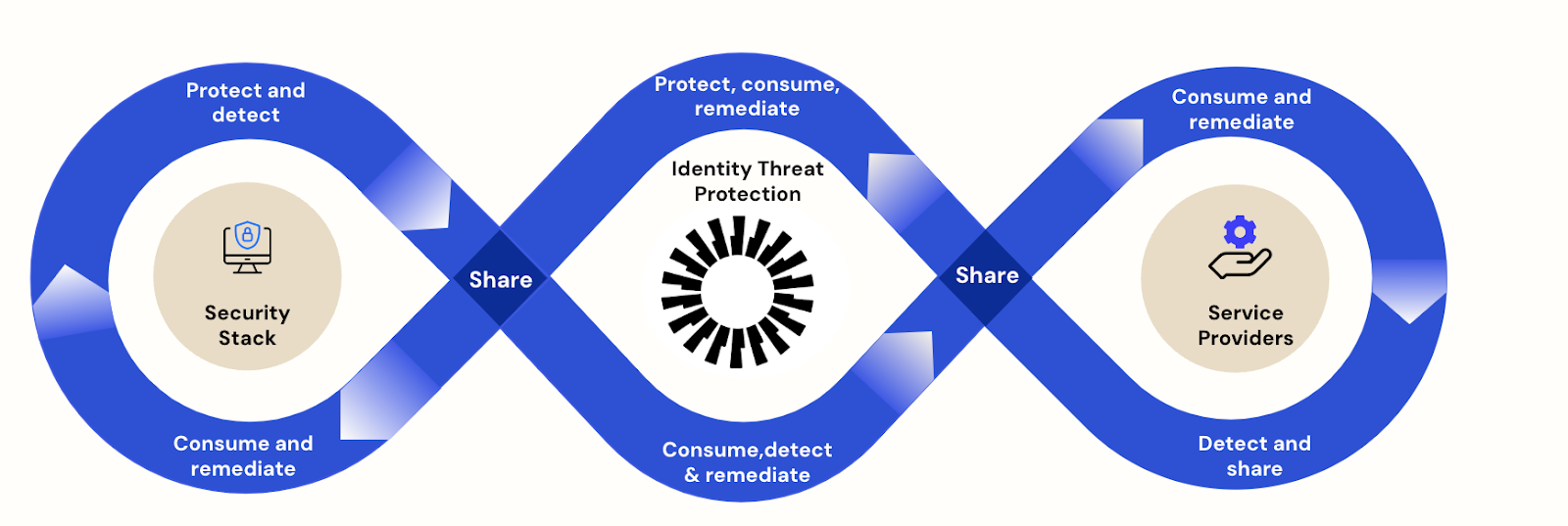
This guidance aligns perfectly with Okta ITP - Identity Threat Protection with Okta AI, which exemplifies enterprise-grade AI implementation for identity security. ITP leverages machine learning models trained on Okta’s global threat intelligence network, analyzing over 2.5 billion authentication events daily to provide:
- Behavioral baseline establishment for each user-device combination
- Real-time risk scoring based on contextual anomalies and threat indicators
- Automated threat response with configurable policies for different risk levels
- Explainable security decisions through detailed risk factor breakdowns for security teams
The integration of NIST’s AI governance principles with Okta’s practical implementation demonstrates how organizations can leverage AI to enhance security while maintaining the transparency and accountability requirements outlined in the federal guidelines.
Conclusions #
NIST SP 800-63-4 represents the definitive maturation of the zero-trust paradigm for identity management, consolidating decades of technological evolution and threat intelligence. The abandonment of legacy practices like forced password expiration, combined with emphasis on phishing-resistant authentication and continuous risk evaluation, sets the new global standard for digital security.
Organizations adopting these principles proactively not only markedly mitigate cyber risk but position themselves strategically to capitalize on digital transformation opportunities by enabling secure and frictionless user experiences that support business agility.
Key insight for executive leadership is that implementing NIST SP 800-63-4 is no longer a nice-to-have but a business imperative. Organizations delaying this transition risk:
- Regulatory compliance gaps with emerging frameworks
- Competitive disadvantages in user experience
- Increased likelihood of security breaches with associated financial and reputational costs
For organizations ready to begin their NIST SP 800-63-4 implementation journey, Okta provides comprehensive resources and proven solutions to transform compliance requirements into competitive advantages.
The next article in this series will dive into SP 800-63A (Identity Proofing) and SP 800-63C (Federation), exploring how NIST SP 800-63-4 redefines identity verification and federation management in multi-cloud, multi-vendor environments, focusing particularly on remote identity proofing requirements and cross-domain assertion management.
Have questions about implementing NIST SP 800-63-4 in your organization? I’d love to hear your thoughts and discuss how these innovations can transform your identity security strategy. Feel free to reach out through the comments or connect with me directly.
-
NIST Special Publication 800-63 Digital Identity Guidelines ↩︎
-
NIST SP 800-63-4, Section 1.2: Structure of Special Publication 800-63-4 ↩︎
-
NIST Special Publication 800-63-4, Digital Identity Guidelines ↩︎
-
NIST SP 800-63A-4, Enrollment and Identity Proofing Requirements ↩︎
-
NIST SP 800-63B-4, Authentication and Authenticator Management ↩︎ ↩︎
-
“Digital Identity Standards.” ENISA, July 3 2023 ↩︎
-
NIST SP 800-63B-4, Section 4: Authenticator Assurance Levels ↩︎
-
NIST SP 800-63-4, Section 5.5: Continuous Evaluation of Risk ↩︎
-
NIST SP 800-63B-4, Section 5.1.1.2: Memorized Secret Verifiers ↩︎ ↩︎ ↩︎
-
NIST SP 800-63B-4, Section 4.2.2: Authenticator Assurance Level 2 ↩︎ ↩︎
-
NIST SP 800-63B-4, Section 5.1.7.2: Multi-Factor Cryptographic Software Verifiers ↩︎ ↩︎
-
NIST SP 800-63B-4, Section 5.1.3.2: Out-of-Band Authenticator Verifiers ↩︎ ↩︎
-
NIST SP 800-63B-4, Section 5.1.1.1: Memorized Secret Authenticators ↩︎
-
NIST SP 800-63B-4, Section 5.2.5: Single-Factor Cryptographic Software Authenticators ↩︎
-
NIST SP 800-63B-4, Section 5.1.7.1: Multi-Factor Cryptographic Software Authenticators ↩︎
-
NIST SP 800-63B-4, Section 6: Authenticator Lifecycle Management ↩︎
-
NIST SP 800-63B-4, Section 5.2.6: Single-Factor Cryptographic Hardware Authenticators ↩︎
-
NIST SP 800-63B-4, Section 5.2.3: Biometric Authenticators ↩︎
-
Microsoft. “Windows Hello security guidance.” Windows Hardware Dev Center ↩︎
-
Google. “Android StrongBox Keymaster.” Android Developers ↩︎
-
Cifas Newsroom, May 7, 2025 “1055% surge in unauthorised SIM swaps as mobile and telecoms sector hit hard by rising fraud.” ↩︎
-
“2024 Data Breach Investigations Report” Verizon, 2024. ↩︎
-
SANS Institute. “Incident Response Survey Results.” SANS, 2024 ↩︎
-
ISACA. “Digital Identity and Trust in the Digital Age.” ISACA, 2024. ↩︎
-
Gartner. “Market Guide for Identity Governance and Administration.” Gartner, 2024. ↩︎
-
Forrester. “The State of Enterprise Identity.” Forrester Research, 2024. ↩︎
-
IDC. “Identity Management Platform Market Analysis.” IDC, 2024. ↩︎
-
Ponemon Institute. “Cost of Identity Management Study.” Ponemon Institute, 2024. ↩︎
-
Okta. “The State of Secure Identity Report.” Okta, 2024. ↩︎
-
NIST IR 8547 (Initial Public Draft), Transition to Post-Quantum Cryptography Standards ↩︎
-
Okta Ventures. “Request for Builders: Five key focus areas in Identity and security.” Okta Blog, April 2025. ↩︎
-
NIST SP 800-63-4, Section 3.8: Artificial Intelligence and Machine Learning in Identity Systems ↩︎

